What is Passwordless Authentication?
Passwordless authentication is an authentication method that allows a user to gain access to an application or IT system without entering a password or answering security questions
MFA Fatigue Attacks: How to Safeguard Your Data and Network
Cybersecurity is a never-ending battle, with network protection and data security at its core. In an era marked by digital advancements and evolving cybersecurity threats, the sign
Strategic BYOD Management: The ‘Why’ and ‘How’ for Businesses
The workplace is evolving at a rapid pace, and one of the notable changes is the proliferation of Bring Your Own Device (BYOD) policies. While BYOD empowers employees with flexibil
Does AI Disruptions Pose Threats to the Traditional Workplace
Artificial Intelligence (AI) stands at the crossroads of transformation and disruption for the traditional workspace. This technology has the potential to bring both risks and rewa
Digital Trust: Technology as a Service
Technological solutionism — the idea that tech developers can be trusted to innovate or code our way out of problems, and into prosperity is on its way out. People’s trust in t
The Utilization of Emerging Technologies as a Service
The utilization of emerging technologies a service provides a competitive advantage to XaaS (Anything as a Service) adopters who leverage service-based IT for access to state-of-th
How to Build IoT Solutions Using Microsoft Azure IoT
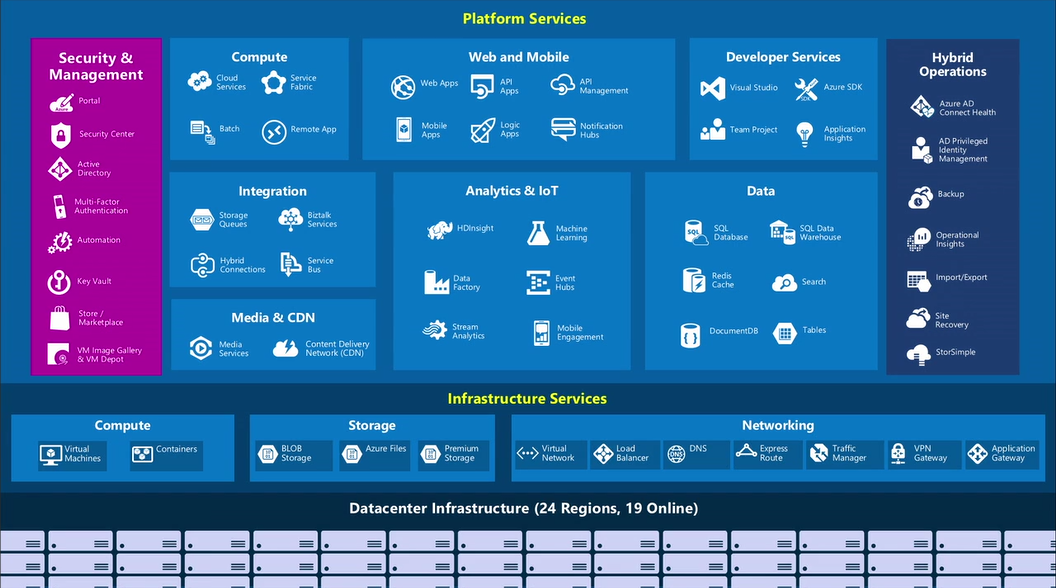
Building IoT solutions using Microsoft Azure IoT can seem like a complex task, but with the right guidance, it becomes an accessible and powerful endeavour. Microsoft’s Azure
Introduction to Azure IoT
The Internet of Things (IoT) industry has continued to expand and permeate people’s daily lives over the past few years. There are many useful applications for IoT devices an
Introduction to Azure IoT Edge
Microsoft Azure IoT Edge is the technology from Microsoft for building Internet of Things (IoT) solutions that utilize Edge Compute. In the world of the cloud, the Edge Compute (ak
Demystifying Identity and Access Management
In the ever-evolving landscape of cybersecurity, few topics have gained as much prominence as Identity and Access Management (IAM). It’s a term that frequently appears in dis