
Demystifying Identity and Access Management

In the ever-evolving landscape of cybersecurity, few topics have gained as much prominence as Identity and Access Management (IAM). It’s a term that frequently appears in discussions about data breaches, compliance, and the protection of sensitive information. Yet, despite its critical role, IAM often remains shrouded in complexity, leaving many wondering: What exactly is Identity and Access Management, and why is it so essential in today’s digital world?
Identity and Access Management (IAM) is a framework of business processes, policies, and technologies that enable the management of digital identities and their access to resources. IAM is essential for ensuring that only the right people have access to the right resources at the right time.
Components of Identity and Access Management
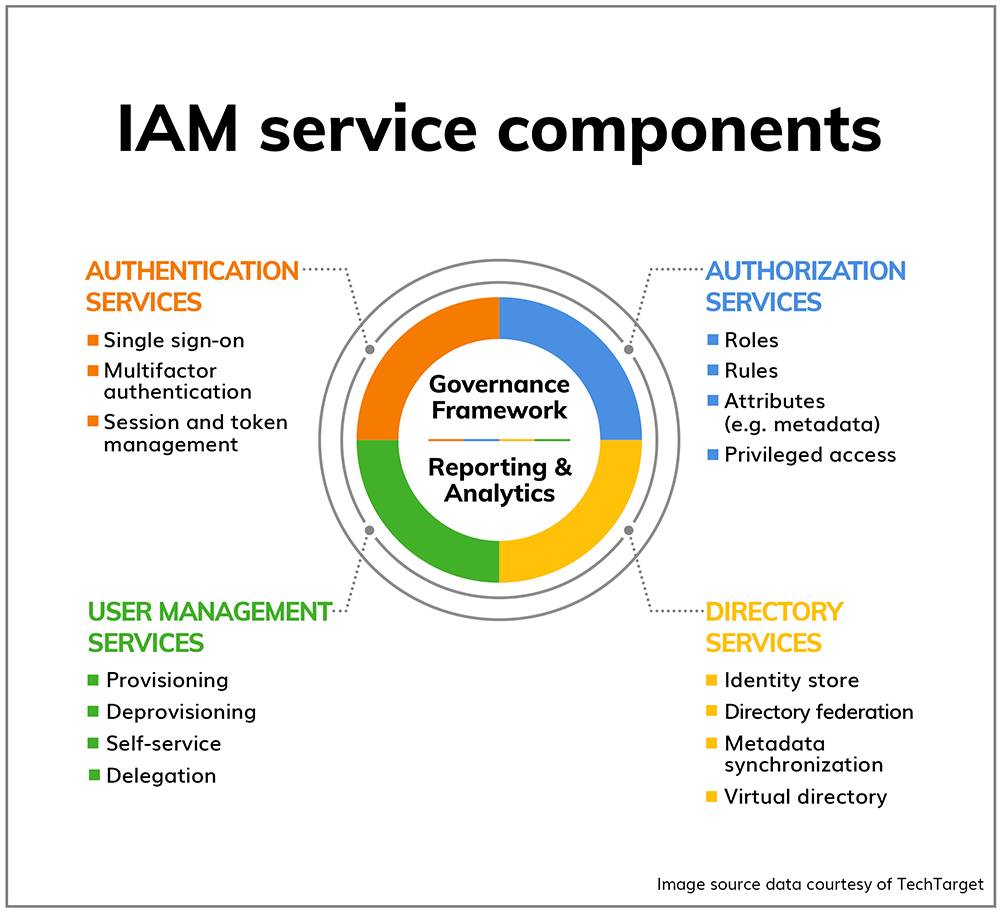
IAM systems typically include the following components:
- Authentication: The process of verifying the identity of a user. This can be done using a variety of methods, such as passwords, two-factor authentication, and biometric authentication.
- Authorization: The process of determining what resources a user has access to based on their identity and role.
- User management: The process of creating, modifying, and deleting user accounts. This includes managing user attributes, such as name, email address, and job title.
- Central user repository: A database that stores all user information, including their identity, authentication credentials, and authorization information.
Benefits of Identity and Access Management
IAM provides a number of benefits to organizations, some of which includes:
- Improved security: IAM helps to protect organizations from unauthorized access to their resources. By verifying the identity of users and controlling their access privileges, IAM can help to prevent data breaches, malware infections, and other security incidents.
- Increased compliance: IAM can help organizations to comply with industry regulations and standards, such as GDPR and HIPAA. By implementing strong IAM controls, organizations can demonstrate that they are taking steps to protect their data and systems.
- Reduced IT costs: IAM can help organizations to reduce their IT costs by automating user management tasks and streamlining access control. IAM can also help to reduce the number of support tickets that IT departments receive.
Identity and Access Management Implementation
The implementation of IAM can be complex and challenging, but it is an essential investment for any organization that wants to protect its data and systems. There are a number of IAM solutions available, both on-premises and cloud-based. Organizations should choose an IAM solution that meets their specific needs and requirements.
Identity and Access Management Best Practices
There are a number of best practices that organizations can follow when implementing and managing IAM, including:
- Use strong authentication methods: Organizations should use strong authentication methods, such as two-factor authentication, to verify the identity of users.
- Implement role-based access control: Organizations should implement role-based access control, which assigns permissions to users based on their roles. This helps to ensure that users only have access to the resources they need to do their jobs.
- Regularly review user permissions: Organizations should regularly review user permissions to ensure that they are still appropriate. This is especially important after changes to job roles or organizational structure.
- Use a central user repository: Organizations should use a central user repository to store all user information. This helps to simplify user management and improve security.
- Educate users about IAM: Organizations should educate their users about IAM and best practices for security. This includes teaching users how to create strong passwords, how to spot phishing emails, and how to report suspicious activity.
Identity and Access Management (IAM) is an essential framework for ensuring the security and compliance of organizations. By implementing and managing IAM effectively, your organization can protect its data and systems from unauthorized access and reduce its risk of cyberattacks.
